They Call It a Royale with Cheese: What GDPR Means for Australia
‘The new European General Data Protection Protection Regulation (aka ‘GDPR’) brings to mind John Travolta’s conversation with Samuel L. Jackson in Pulp Fiction where Vincent (Travolta) muses to Jules (Jackson):
But you know what the funniest thing about Europe is?...It’s the little differences. A lotta the same **** we got here, they got there, but there they're a little different…”.
Jules
“But you know what the funniest thing about Europe is?...It’s the little differences. A lotta the same **** we got here, they got there, but there they're a little different…”.
Jules: “They don't call it a Quarter Pounder with Cheese?”
Vincent: “No, they got the metric system there, they wouldn’t know what the **** a Quarter Pounder is”.
Jules: “What'd they call it?”.
Vincent: “They call it a Royale with Cheese”.
They call it a Royale with Cheese”.
Vincent
They call it GDPR.
Things are a little different in Europe. The GDPR is the biggest change in data protection laws in Europe since the introduction of the European Union (EU) Data Protection Directive in 1995. European data protection law aims to protect individuals’ privacy and personal data. The GDPR introduces a common standard for how firms that operate in the EU should protect the personal data of their customers, employees and suppliers. The GDPR is essentially a response to the unprecedented volumes of personal data currently generated by increasingly rapid technology adoption and the host of new cyber security threats that come with digitisation.
The GDPR will require significant technology investment and remediation to meet various new governance requirements and expected technology capabilities. Critics of the GDPR argue that the new rules are complex and vague and have been constructed in a vacuum without consideration of the practical challenges or cost involved in adhering to the new requirements. The broad territorial scope of the GDPR means that it will apply globally to any organisation doing business in the EU or selling products or services to EU citizens and collecting EU citizens’ data.
GDPR non-compliance carries heavy fines. Some infringements of the GDPR could mean a penalty of up to 4% of annual worldwide turnover or €20 million, whichever is higher. It is estimated that FTSE 100 companies could face fines of up to £5 billion a year if they don’t comply with the GDPR.
The GDPR will apply from 25 May 2018 and so, with less than a year left to prepare, the countdown is now on for many Australian global enterprises that will inevitably be impacted by the GDPR’s wide reach.
Key findings of various recent surveys[1]of senior executives in leading global companies show that around 60% of respondents were not fully aware of the GDPR; preparation for GDPR is expected to be extremely time consuming; and most organisations are not yet GDPR ready (less than half are confident that they will be ready for the compliance deadline in 2018).
Clearly, there is yet a lot of work to be done by many organisations across the globe to ensure GDPR compliance. From a technology perspective, the GDPR poses many challenges (discussed in more detail below) and will put IT departments on high alert to safeguard personal information across all tiers of the environment.
In this article, we consider why Australian enterprises should worry about the GDPR and act now. We also highlight the practical technology challenges posed by GDPR requirements and explore several potential solutions and approaches that form the building blocks of GDPR compliance.
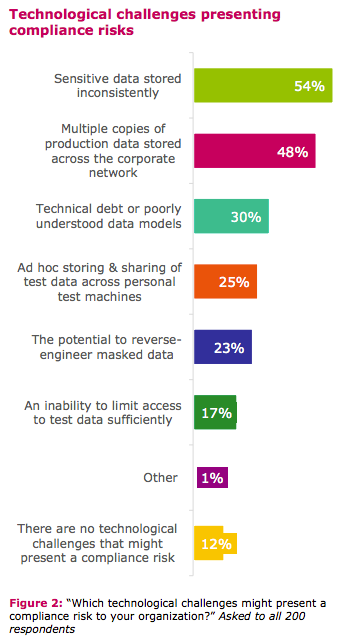
Source: “EU GDPR: Are You Ready For it” by CA Technologies.
Why should Australian enterprises worry about the GDPR?
GDPR has an extra-territorial impact that will affect any organisation that deals with European customers, regardless of where that organisation is based. Global Australian enterprises will therefore be caught by the GDPR if they have an EU office/presence, and/or offer goods or services to EU citizens (i.e. target EU consumers) and/or they collect data from (or monitor) their European customers.
There are some common elements between the GDPR and existing Australian privacy laws, e.g.: the privacy by design approach to compliance; the requirement to comply with privacy principles; and adopting transparent information handling practices. Additionally, data breach notification and privacy impact assessments, mandated in certain circumstances under the GDPR, are expected in similar circumstances in Australia. Both laws are also technology neutral (i.e. no specific tools or architecture are mandated by existing regulations and these are left to the organisations’ discretion).
However, there are some elements of the the GDPR, notably individuals’ rights (such as the right to be forgotten and the data portability right), which do not have an equivalent under Australian law.
Given the broad similarities between EU and Australian laws, Australian businesses may already have some of the measures in place that will be required under the GDPR. However, they should take steps to evaluate their data handling practices and governance structures to implement the necessary changes well before commencement of the GDPR in May 2018.
Australian businesses could consider rolling out any additional GDPR-compliant processes/tools across their Australian operations as this could improve consumer trust through enhanced privacy practices and allow for more consistent internal privacy practices, procedures and systems across the business globally.
How would Australian enterprises be impacted?
The key new requirements introduced by the GDPR, which may apply to Australian enterprises, are:
- Carrying out a data protection impact assessment (DPIA) for certain risky data processing activities and incorporating data protection by design and default into products and services (e.g. data minimisation);
- Appointing a Data Protection Officer (e.g. if you process certain data categories on a large scale);
- Applying a higher threshold than currently exists for customer consent regarding the processing of data - organisations would have to ensure that such consent is freely given, informed and unambiguous and customers will have the right to withdraw consent to any data collection, at any time;
- Data breaches would have to be notified to the relevant data protection authority within 72 hours of the organisation becoming aware of the breach. In some cases, customers affected by the data breach would also have to be promptly notified; and
- Customers will be entitled to ask for access to their data, or for their information to be transferred to another company (called the “data portability” right) and will have the “right to be forgotten” (i.e. customers can ask that their information be erased “without undue delay”). The organisation would have to respond to such requests within one month in most cases.
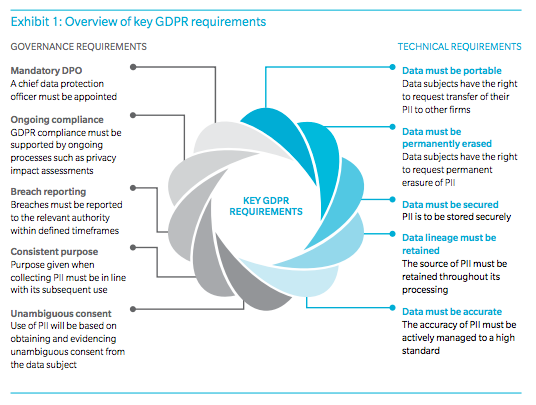
Source: “Future Proofing Privacy: GDPR Compliance in a Networked Banking System” by Oliver Wyman
High stakes in financial services
All impacted organisations will need to work out what data they hold on their customers, where they hold it, if they have permission to do so, whether it is stored safely, and how they can extract it in an easily “portable” form or erase it altogether, if requested by customers. However, the impact on financial services firms, in particular, will be significant.
FS firms typically serve millions of customers, deal in complex products that require access to customer data, have intricate supplier networks and employ a large global workforce. It is well-known that FS firms often have outdated and patched-together legacy systems leading to duplicative customer data stored across multiple systems (which may extend to more than 100 systems in some banks!). Many of those systems have never been considered from a data protection perspective and changes to them can take a long time to implement.
This is further complicated by the fact that banks have been forced by competition authorities to open up and provide third party vendors with access to customer data, and economic factors have historically led to greater use of outsourcing, with sensitive data being sent to third party providers. At the same time, financial crime regulation resulted in banks collecting as much information on customers as possible.
FS firms are therefore - inevitably - in the GDPR firing line. Simply put, the more personal data a firm collects, processes and shares with others, the more significant the GDPR requirements become and the more serious the exposure to cyber security threats. Given their size and IT systems complexity, many FS firms have incomplete infrastructure and relatively undeveloped defences against privacy breaches.
We are seeing that FS firms are seriously concerned over whether they can meet the May 2018 GDPR deadline[2], warning that the challenges of overhauling complex, legacy IT systems in preparation for GDPR could prove insurmountable. The survey also showed that 76% of respondents believe they face serious challenges in complying with GDPR[3]. Customer's’ right to be forgotten (i.e. for their data to be erased) and security of data processing were quoted as some of the biggest hurdles facing the banks.
According to a recent survey of 500 IT decision makers of financial services firms in the UK, France, Germany and the US[4], banks have the most to lose from non-compliance with the GDPR as they are the most likely organisations to be made an example of by regulators in the event of a GDPR breach.
It is clear that many Australian banks (and other FS firms in Australia) will be affected by the GDPR, and therefore it will be vital for them to have robust systems and processes in place, in order to meet the extensive regulatory obligations and avoid huge the fines for non-compliance.
Is Australia ready?
As Australian organisations are getting to grips with the GDPR requirements and their operational implications, it is forecast that they will each spend nearly $2 million on GDPR preparation.[5]
The Office of the Australian Information Commissioner has issued a useful briefing on the GDPR and what it means for Australian businesses. However, recent surveys worryingly show that less than 30% of Australian organisations believe that are currently compliant with the GDPR, and 46% are concerned they may not be able to meet the compliance deadline of 25 May 2018. Around 90% of APAC businesses said they did not know much about the GDPR.[6]
One of the main factors hindering compliance is said to be a lack of technology tools capable of addressing the regulatory requirements, with 30% of respondents worried that their current technology stack is unable to manage their data effectively and 39% reported an inability to accurately identify and locate relevant data.
Aside from high fines, there are reputational and commercial risks associated with non-compliance with the GDPR (e.g. layoffs, brand devaluation, loss of customers etc.). With the number of high profile data breaches steadily increasing globally, data protection regulation will likely become a priority issues for many global businesses, the mishandling of which could have a severe financial and reputational cost. Also, with a new Australian mandatory data breach notification law expected to apply in early 2018, it is no wonder that many firms are under pressure to come up with a sustainable privacy and data protection compliance plan.
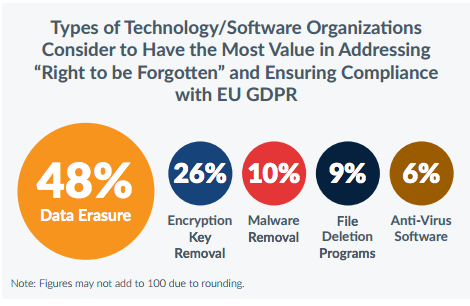
Source: “EU GDPR: A Corporate Dilemma. A Study on Corporate Readiness To Remove Customer Data” by Blancco Technology Group.
GDPR compliance - Technology as a driver
Companies should address the GDPR requirements now and put in place a robust compliance roadmap. An effective GDPR compliance plan should focus on technology as a compliance driver to enable active privacy and data management across the organisation’s entire ecosystem. Here are the main technology challenges ahead and what could be done to address them:[7]
1. DATA MAPPING & LIFECYCLE MANAGEMENT
- Firms must have a complete understanding of the organisation’s data and processing activities. Under the GDPR, organisations will have to maintain records of the categories of individuals whose data are processed, the categories of data that are processed, the categories of recipients of the data and their geographical whereabouts, the retention periods that apply to the data, and the security measures applied. These records will be disclosable to the regulators on request.
- Firms must also dispose of personal data which is not being stored for a legitimate purpose, is not accurate, has exceeded its retention period, or where consent from the data subject does not exist.
Challenges:
Managing legacy data and applying adequate data lifecycle management on older platforms and applications that have been organically extended and designed without data protection considerations in mind.
- The ability to search and rapidly identify customer data is vital for all use cases:
- A subjects right to rapid notification in a data breach scenario.
- A subjects right to data portability.
- A subjects right to request access or erasure of the data (right to be forgotten).
- Fulfilling reporting requirements and supplying information to the relevant local data protection authority.
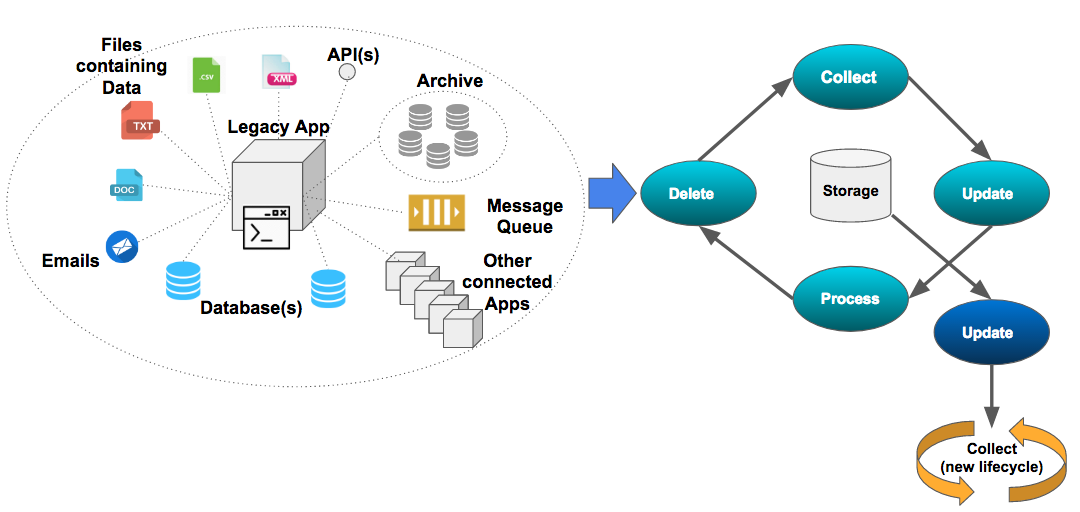
- The scope of what data would be considered personally identifiable information (PII) is extremely broad, firms must consider the subjects data itself, it's complete history (lineage), how it was acquired (origins), if it was masked/deleted/updated and the reasons why, where/who has this been distributed.
- Older applications with multiple data instances and disparate, inconsistent customer data sources warrant significant consideration.
- Identifying, gathering and reconciling data will be challenging (and, in some cases, near impossible to execute quickly) when a customer requests data erasure or porting data to another institution.
- A common example would be an older legacy mainframe banking application which may contain key customer data that is not visible to the customer service teams. While the most visible and ‘active’ customer data might exist in a modern CRM platform (such as Salesforce), GDPR requires all customer personally identifiable information (PII) to be quickly identified and actionable across all systems. PII may be contained in archived backups of system records, data warehouses, analytics data, files, emails, configuration, multiple platforms/servers each with slightly different variations. A related challenge will be how to isolate one individual’s PII from other customers’ records.
- The way in which data is synced, distributed and propagated across applications or platforms is also a source of potential inconsistencies and should be factored into the end solution.
- The GDPR sparks debate around the right reference data architectures (ie Data Warehouse, Master Data management, expensive 3rd party reference data management systems etc). Firms already struggle with current compliance requirements and so future-proofing their architecture to meet additional unknown requirements presents an additional challenge. It is therefore critical that firms start by systematically identify all data locations and all affected processes.
Suggested Action(s)
- Define what, where and how personal data flows and is stored across the organisation.
- Establish a comprehensive data lifecycle process, including a secure data removal functionality when needed.
- This means having data discovery and mapping capabilities as well as consent management systems to identify, rectify, anonymise, delete, pseudonymised, suppress or encrypt the data. Archive management tools are also needed to ensure personal data is not being retained inadvertently within archives and backups.
- Develop a comprehensive data strategy and a data protection policy - treat all consumer personal data with the same care as passwords, credit cards and confidential information.
- The challenge of mapping data is complex as “a full chain of custody” for each data element needs to be maintained. Organisations require a full audit trail via a central register of activity related to each data element. The audit of activity could be used as a reference point to document the origin of the data and and which systems or 3rd parties it has been assigned to. In the case of a mistake or abuse, the central register could provide a record of what happened. Linkedin’s opensource “WhereHows” data discovery and lineage tool is an example of one approach to this problem. Other commercial solutions in this space include Denodo, Exonar, Titus and BlueTalon (although we cannot advise which tool would be most suitable to your specific circumstances).
- Next generation platform technologies like AWS’ EBS, S3 and RDS are CISPE compliant offer strong choices for intelligent, robust data storage that enable secure tracking and management of customer data.
- Consider adopting tokenisation and encryption best practices for the storage of all data. Technologies such as Delphix are excellent examples of efficient and innovative ways to mask, tokenise, virtualise data sources thereby simplifying how data can be managed across Dev, Test and Prod environments without compromising compliance requirements.
The challenge of managing legacy data
2. RISK MANAGEMENT & COMPLIANCE
Conduct privacy impact assessments (PIA) to understand the data protection risk coming out of your data processing activities and the wider environment in which you operate. technical and organisational measures.
Challenge(s):
For privacy impact assessments to be effective, the organisation must gain a deep understanding of its technology’s privacy impact and the risk posed by its existing data practices.
This will involve reviewing any risky processing activities and taking steps to address specific technology gaps and concerns coming out of those assessments. Organisations will need to find a way to translate data protection principles and regulatory requirements into technology solutions and implement appropriately.
Furthermore these processes need to be applied continuously to all changes (process or technology related).
Suggested Action(s):
- Adopt systems to help manage PIAs, identify risk gaps and establish a compliance record.
- Establish systems to manage customers’ data requests/complaints, manage the data control framework for all elements of PII collected data.
- Adopting robust training solutions or systems to ensure practices alignment across the organisation, operational consistency and that you can demonstrate staff GDPR understanding and compliance.
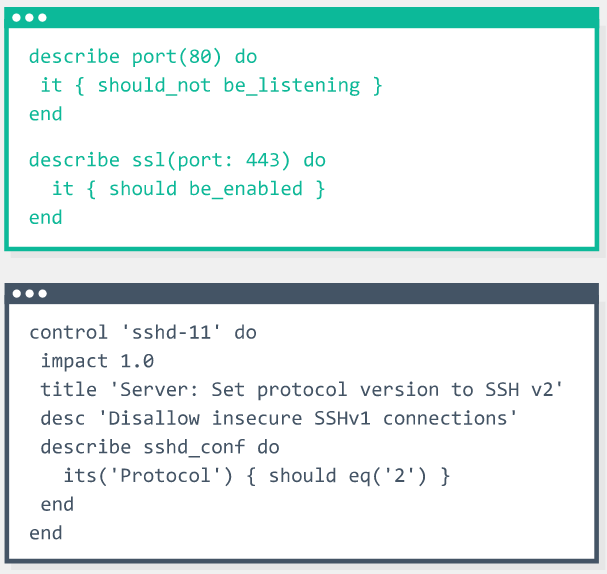
- Adopting “Compliance-as-code” model to automate manual compliance checks and balances within the technology stack is essential for maintaining rapid delivery capability and competitiveness whilst also ensuring consistency and integrity of compliance requirements. These models ensure that security and compliance elements are codified and embedded into products early on, using tools like Chef’s Inspec. Automating checks related to personal data collection, customer controls and the presence of privacy policies within the application development process is essential.
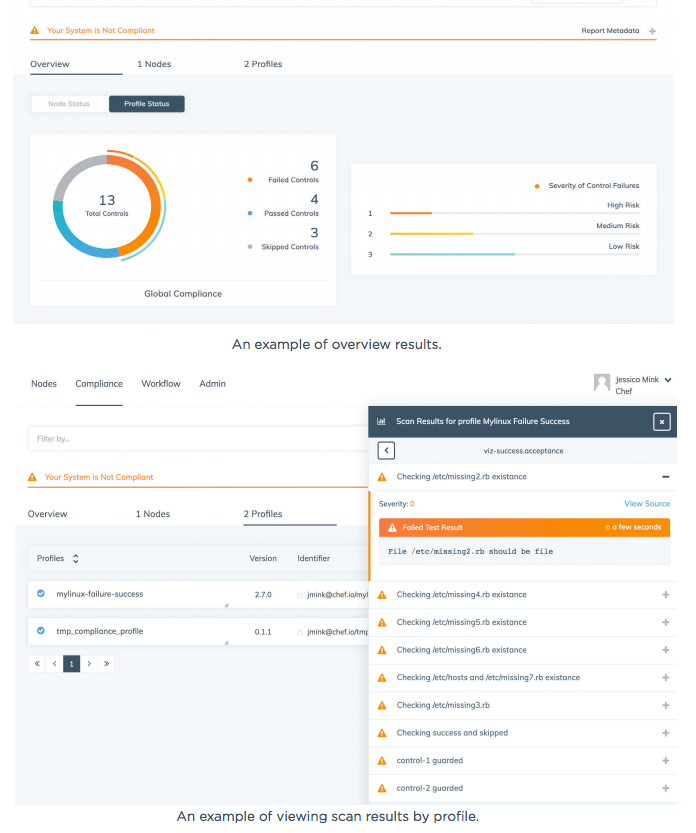
Chef Inspec compliance-as-code example where application compliance checks are defined in codified rules.Results of the compliance checks can be viewed on a Chef compliance dashboard.
Results of the compliance checks can be viewed on a Chef compliance dashboard.
3. PRIVACY BY DESIGN
Ensure that privacy is embedded into any new processing or product that is deployed from the start, and generally minimise data processing and retention, as well as build in appropriate safeguards. Data protection should be consistently baked into any new products builds, services rolled out and tools utilised across the company and this should be done from the outset rather than an afterthought.
Challenges(s)
- Some organisations may need to entirely redesign their data collection and data protection programs as well as their product and services development process.
- Data processing systems should process only the minimum of amount of personal data required to deliver the processing purpose. This means that firms should limit the types and volume of personal data that are processed, and reduce the number of times that processing occurs as well as the retention period for the data. It also involves reducing the number of people, the number of entities and the number of technology systems that can access the data.
- Clearly, this has implications for legacy systems which have never been considered from a data protection perspective.
Suggested Action(s):
- As a starting point, it is critical that organisations embrace advanced integrated access control like that of AWS’ AWS Identity and Access Management (IAM) to provide fine-grained control of manage users, groups assigning explicit permissions to allow and deny access to resources. Access control best practices need to also be applied to the data lineage systems, key meta-data related to subjects need to treated as sensitive data - should be tightly controlled, encrypted and obfuscated where appropriate. Data virtualisation techniques and well considered data strategy (how data is distributed throughout an organisation) is critical.
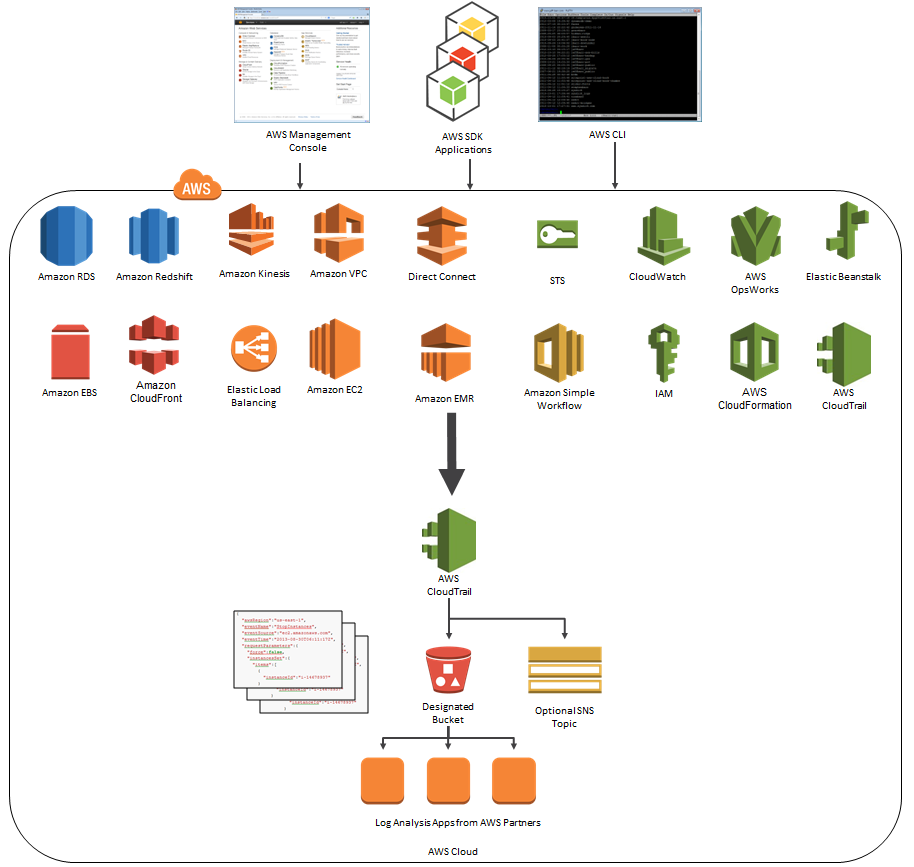
- Comprehensive audit and logging strategy covering all resources - Application, Platform, Data, network and Storage are baked into the DNA of the stack Tools like Amazon’s CloudTrail.
- New systems and processes deployed should:
- Protect data through the use of encryption, pseudonymisation etc.
- Manage data quality and enable deletion as a key functionality.
- Detect, manage and resolve breaches in real time.
- Manage & coordinate data coming in from multiple channels.
- Manage archive data and enable its deletion in accordance with data retention policies.
- In order to embed privacy and security into the existing technology stack, organisations need to consider re-platforming (or re-writing) applications. Technologies like Cloud (AWS, Azure, GCP), containers (ie Docker, Kubernetes) and Serverless offer greater flexibility and integration opportunities over traditional modes of application deployment.
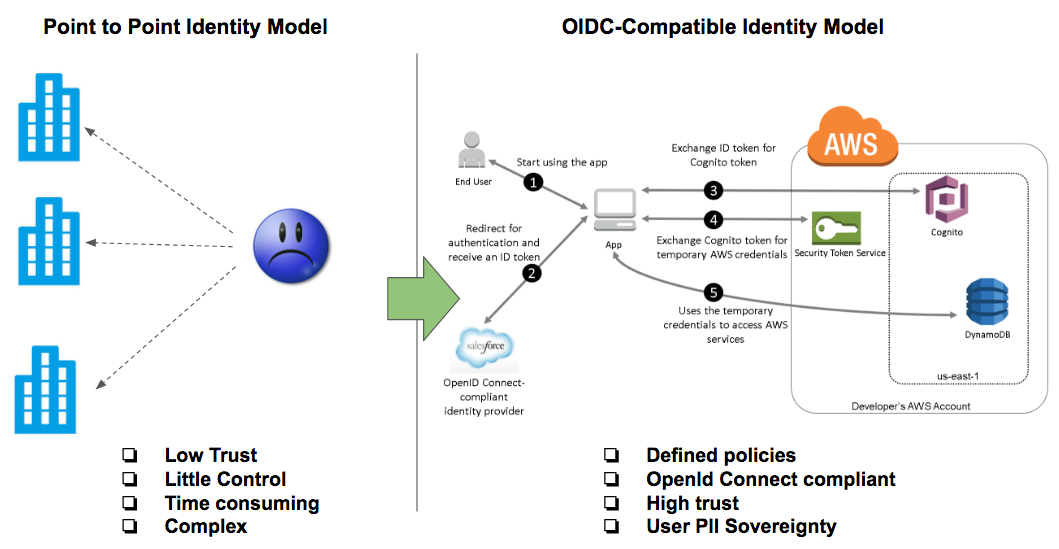
Organisations need to offer customers and users more secure token-based authentication models like OpenID Connect instead of traditional point to point identity models.
4. INTEGRATION
Ensure that the organisation’s technology environment is prepared for data subjects to exercise their rights under the GDPR (e.g. the right to data portability and the right to data erasure).
Challenges:
Organisations will need to put in place a suitable process for the management and execution of portability and erasure requests from users and data owners.
The technology utilised should allow organisations to be responsive to such requests through accurate mapping of the type of information collected, the ability to search and retrieve it, and adequately enable data to be erased, updated or transitioned, as required.
Suggested Action(s)
- Organisations should move towards models that allow for self-sovereignty of personal identifiable information (PII). Interfaces should be redesigned to explicitly capture customer consent (sign-up).
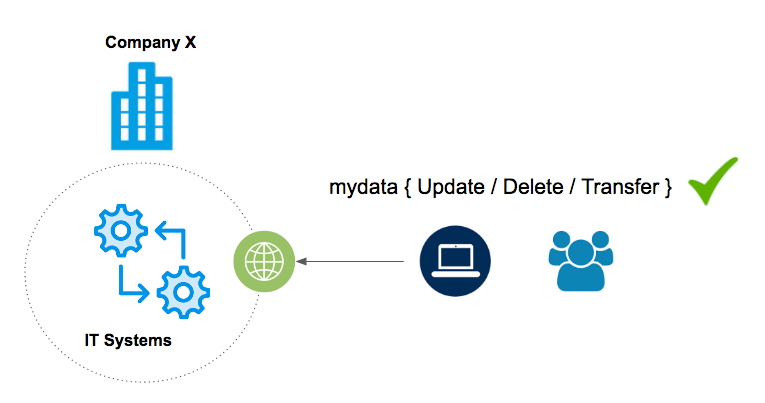
- Ongoing management of subject data can be achieved through development of subject access portals that allows customers to take control of their own data, providing a single access point through which to provide, change and revoke consent for use of private data. Some have suggested this is another potential application for a distributed ledger system spawning “blockchain privacy” applications.
- Integrating the existing systems with the centralised data registry or ledger (data chain of custody).
- Other considerations include integration points with external 3rd party data sources and/or vendors. All activity related to the lineage of data would be tracked via the centralised chain of custody.
- DevOps and automation best practices will need to be baked into these data management processes to minimise human error and meet time-sensitive deadlines where action is required. Tools like the AWS platform, orchestration tools suach as Chef, Puppet, Ansible, Saltstack and Hashicorp’s Terraform are excellent frameworks to enable execution complex tasks within a complex distributed environment.
Example application that would allow users to manage their own data via a web portal
5. SECURITY
Prepare for breach notification - GDPR requires organisations to regularly test, assess and evaluate the effectiveness of technical and organisational measures for ensuring the security of data processing.
On the breach notification side, companies must notify the nature of a breach, the volumes of data and people affected, information about the likely consequences and measures taken to address the breach and mitigate harm.
Challenge
Eliminating threats is impossible, so protecting against them without disrupting business innovation and growth is a top challenge. Certain trends make data ever more difficult to secure and an increasingly attractive target to cybercrime: more online transactions take place globally and more pervasive data is being collected by companies for insight and marketing purposes; corporations are expected to be more open than ever before and BYOD is prevalent; supply chains are ever more interconnected; and cybercriminals are becoming more sophisticated.
Suggested Action(s)
- Continuous monitoring is an essential component to safeguard against today’s dynamic cyber threat landscape. AWS Cloudtrail allows organisations to seamlessly aggregate and monitor all events, logs, activities so that they can be effectively monitored. Next generation security models can take corrective or preventative measures when suspicious or potentially problematic events have occurred. Disparate traditional apps with no centralised logging open the door to widescale undetected breaches.
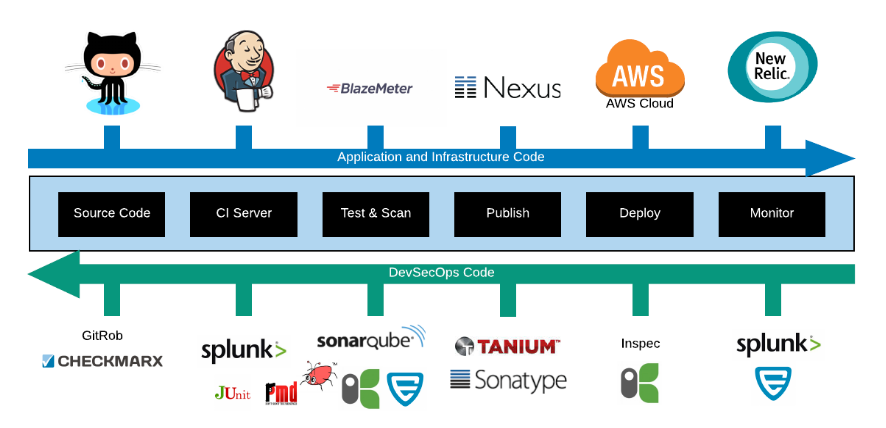
- Leveraging Automated security (DevSecOps) best practices also known as shifting security “left” to ensure security requirements are validated early within the software development cycles. Security vulnerability, licences and rules are codified and validated against code changes when committed to the source code management (SCM) system.
- Applying automation to all aspects of the technology stack, including network elements, is vital for being able to quickly respond to and contain threats. Zero Trust (ZT) networks, micro segmentation techniques (such as Palo Alto Networks products) and Software defined network (SDN) architectures are great innovative examples of enhanced security measures that organisations can employ to further reduce cybersecurity risk and threat response times.
- Staff training and education on GDPR obligations and security practices will help foster a culture of monitoring, reviewing and assessing data processing procedures.
Example DevSecOps Pipeline integrated into s/w development processes
AWS Cloudtrial - used to monitor all actions, events and services within the AWS platform.
Every GDPR has a silver lining
There is no doubt that GDPR will have a game-changing effect on organisations around the world. Despite the inevitable complexities posed by the GDPR, it will undoubtedly be a major driver of data protection and security initiatives vital for fostering customer trust and future proofing security systems. These forces will help prepare global organisations for the future challenges of digitisation and the GDPR will be a significant catalyst for overdue transformation, cloud technology adoption, automation and efficiencies across the board.
It is clear that the short-term hurdles will be substantial, but the GDPR process will serve organisations in the long term - it will force companies to take a long, hard look at their data management practices, reveal technology gaps, encourage much needed technology investment and, eventually, lead to the overall improvement of privacy and security standards, benefiting customers and enterprises alike.
Ultimately, those companies that can boast about GDPR compliance will have a competitive advantage and be rewarded for prioritising security and privacy. The tools and best practices to start that journey are available now.
So with less than twelve months left before GDPR is instated, in the words of Pulp Fiction's 'The Wolf': “You got a corpse, minus a head, in a car in a garage, the clock is ticking”.
You got a corpse, minus a head, in a car in a garage, the clock is ticking."
- The Wolf
References:
1- http://www.ca.com/content/dam/ca/us/files/white-paper/eu-general-data-protection-regulation-gdpr-report.pdf
2- https://www.ft.com/content/ad3916e0-4459-11e7-8519-9f94ee97d996
3- https://info.varonis.com/hubfs/docs/2017-GDPR-survey-results.pdf
4- https://info.varonis.com/hubfs/docs/2017-GDPR-survey-results.pdf
5- http://www.technologydecisions.com.au/content/it-management/news/46-of-firms-worried-about-gdpr-deadline-1179118980#axzz4hV8mPimA
6- http://www.zdnet.com/article/singapore-japan-korea-among-least-prepared-for-new-eu-data-laws/
7- Please note that this article and any suggested steps or actions within it are provided for general guidance and information purposes only and should not be relied on without seeking advice specific to your commercial circumstances and IT environment and systems.


![DevSecOps: A Quick Compliance as Code Demo [Video]](https://cdn.sanity.io/images/hgftikht/production/81d15c6d8669d2cb4c9c0b4422cd5bb87cb07f83-1200x480.jpg?w=630&h=427&fit=crop)


