What Is Compliance as Code? Benefits, Use Cases and Tools
Being compliant in today’s cloud-first world of rapid innovation is a ubiquitous challenge affecting startups and enterprises alike.
Enforcing sets of controls, such as acceptable data storage locations and access control management, and ensuring these are followed at scale is critical to a thriving digital business.
The cost of failing to adhere to compliance rules is serious: On average, a regulatory compliance violation costs businesses nearly 15 million dollars.
While, in the past, it was possible to manage compliance manually, the rapid pace of modern software delivery means that the only true solution these days is compliance as code.
By adopting an engineering mindset, through code you can make compliance automatic, releasing your company to focus on higher value activities.
By the end of this article, you will understand the core compliance loop, how it works in the cloud native era, and what tooling options exist to support you on this journey.
But first, let’s look at what is meant by compliance as code.
What Is Compliance as Code?
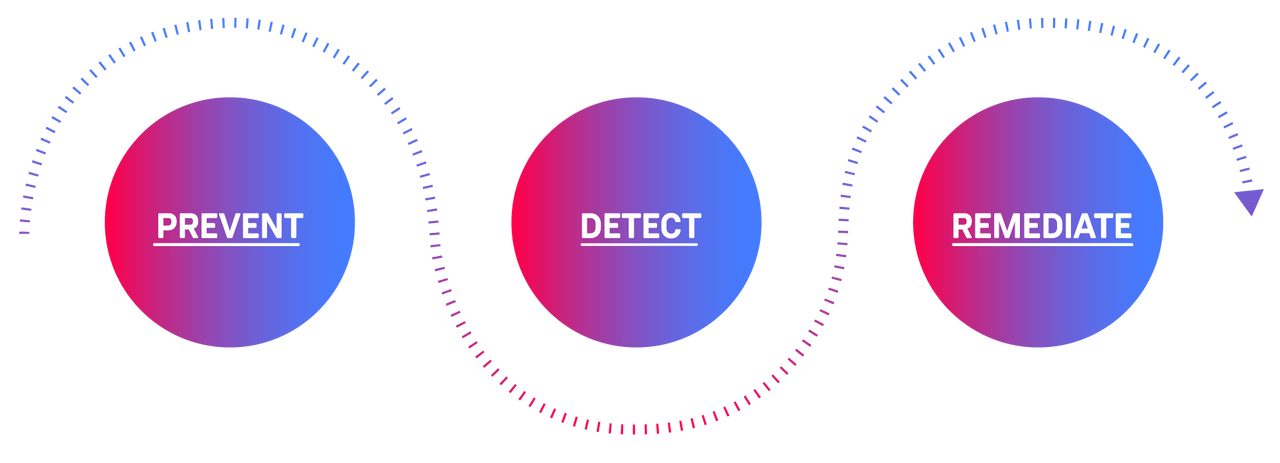
Compliance as code refers to tools and practices that allow you to embed the three core activities at the heart of compliance: Prevent, detect, remediate.
- Prevent non-compliance by automatically asserting planned changes are compliant.
- Detect non-compliance through automated estate scanning, notifying stakeholders when offending infrastructure is identified.
- Remediate non-compliance by making immediate changes to infrastructure to ensure the maximum level of compliance at scale.
Compliance as code can be summarised as the codification of your compliance controls so their adherence, application and remediation can be automated.
Typically, compliance as code tools work by enabling compliance stakeholders to define how IT resources must be configured in order to meet compliance controls. Then, the tools automatically scan or monitor the live IT environment and planned changes in order to detect non-compliant infrastructure. Additionally, compliance as code tools often have functionality that allows them to automatically modify resources into a compliant state.
The configuration languages and formats used to write compliance as code policies vary depending on the compliance as code tools you use. Some tools have their own domain specific languages (DSLs), while others use standardised file types, like JSON.
Unfortunately, as it stands, implementing compliance as code is not as simple as “enforce GDPR compliance”; instead the controls are more fine-grained. An example of a common policy is enforcing data encryption at rest in a cloud provider’s object storage, or ensuring all users have multi-factor authentication configured.
This said, many compliance as code tools come with predefined policy collections that enable trivial enablement of industry standard checks. Amongst the most common offered are CIS benchmarks.
Conceptually, compliance as code is fundamentally the same as other "X as code" initiatives. For example, just as infrastructure as code makes infrastructure standardised, repeatable and reduces manual toil from the process, compliance as code brings these same three core benefits.
Regulatory Compliance Vs. Internal Compliance
Compliance as code is a useful strategy for enforcing both regulatory compliance rules and internal compliance rules.
Regulatory compliance refers to rules mandated by frameworks like the GDPR, HIPAA or PCI DSS, which are regulations that are established by government authorities or industry groups. Failure to comply with regulatory compliance leads not only to immediate financial damage, but long-lived reputational damage as well.
However, compliance as code is not just a method for meeting regulatory controls. You can also embed your own internal IT governance, unlocking potential cost savings and improving your security posture.
The key point to remember is that compliance as code can drive far more impactful outcomes than purely regulatory compliance.
Compliance as Code Benefits
By adopting compliance as code, you can unlock a series of benefits and bring new operational capabilities to the table.
Standardisation and Consistency
Compliance as code helps to establish standards that are applied consistently across your entire estate.
When teams use code to define the compliance rules, they are able to bring unprecedented consistency to their entire estate, no matter the size. Monitoring 1,000 servers is no more effort than monitoring only one.
Mandatory compliance audits, in which human engineers check for compliance violations by hand, cannot deliver with the same level of consistency or accuracy. Controls can be misinterpreted and mistakes can be unintentionally made. Compliance as code prevents ambiguity and treats every resource exactly the same.
Scalable compliance
Compliance as code makes it possible to scale compliance efforts seamlessly as IT environments grow.
The key to scaling IT infrastructure at enterprises is finding solutions that scale sub-linearly, i.e. the effort per resource becomes less as you scale the estate. By implementing compliance as code, the effort to monitor 50 teams is only trivially more than measuring 5. Whereas, if humans are responsible for monitoring compliance, it takes 10 times the effort.
Cost savings
The automation of compliance breeds cost savings too.
It does this in two ways:
- By automating compliance, you can achieve better compliance results with fewer staff. Security experts command very high salaries, and are in high-demand across the industry. By using compliance as code you can magnify the impact of your security team so they can focus on higher value initiatives.
- Through holistic monitoring of compliance, you significantly reduce the risk of fines and data exposures in your business.
Keeping compliance up to date
Compliance rules change constantly:
- New regulatory compliance frameworks may appear (like the CPRA, which is in the process of replacing the CCPA)
- Existing frameworks may be updated.
- Court rulings could impact the way existing regulatory rules are interpreted, necessitating changes in compliance workflows.
- You may also need to modify your internal IT compliance rules due to business changes or the adoption of new IT strategies.
Whenever a change to your compliance regime happens, through compliance as code, you can quickly understand all areas of emergent non-compliance, and quickly remediate all identified issues.
With manual compliance, you need to retrain all of your team members and retool your monitoring processes, which would require a far larger time investment, and would leave you vulnerable for longer.
Unity between developers and risk-assessment teams
When compliance controls are defined as code, delivery teams naturally become more aligned to the compliance process. Through their codification, the controls become more understandable and real.
With compliance as code, you can embed the rules into your teams’ delivery processes. Rather than allowing for ambiguity and misinterpretation to undermine your compliance efforts, you can utilise a common vector to enable delivery to be compliant by default.
Continuous compliance
When compliance rules are defined as code and can be enforced automatically, it becomes possible to continuously detect non-compliant infrastructure but also to prevent the infrastructure from being created.
Through the adoption of infrastructure as code, combined with compliance as code, it becomes possible to analyse pending changes to your cloud estate and prevent non-compliant changes from ever being applied. This–blended with an ability to scan live infrastructure–gives you the ability to improve compliance and make the changes enduring, as opposed to regressing over time.
Compliance as Code Examples and Use Cases
The potential of compliance as code grows as the industry matures. The use cases that will drive the most impact at your business, depend on three key things: the infrastructure choices you make, the regulations you must abide by and the control set you adopt.
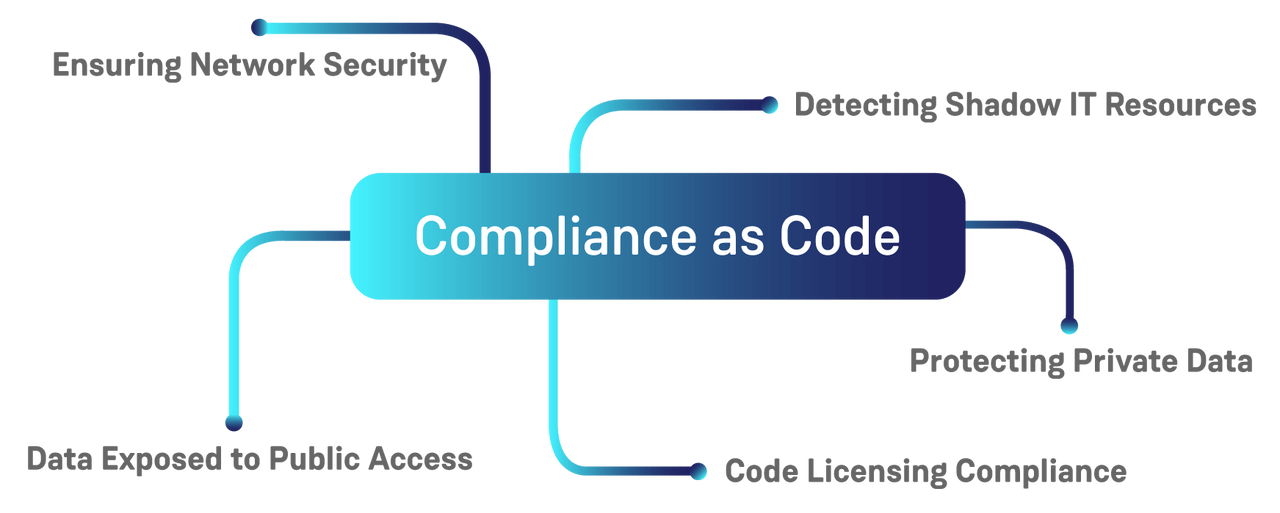
Protecting private data
As an example of compliance as code at work, imagine a company that is subject to privacy regulations (such as GDPR or HIPAA) that mandate certain steps to secure personal data. Those steps include ensuring that only authorised parties can access the personal data.
To help meet this control , the company's IT team writes a policy that evaluates which access control rules are in place for personal data.
Once that policy is enabled across the estate, the team can discover where PII data is being stored with insufficient controls, such as insufficiently restricted network connectivity or encryption not being up to the required standard.
At a minimum, the tool generates an alert allowing for manual remediation to occur, in a mature organisation the database is immediately modified to conform to the requirements set out in the policy.
Detecting shadow IT resources
As another example, a compliance as code policy can detect the existence of IT assets, e.g. virtual machines, that have been provisioned outside of the authorised channels. In this way, compliance as code tools identify shadow IT assets, and can help not only improve your security posture and infrastructure bill, but also bring symptoms of cultural issues to light.
Data exposed to public access
It’s unfortunately commonplace in modern cloud, to inadvertently open up data for public access. That’s because historically, a lot of defaults in the cloud have been about making things easy over making things secure. The “S3 Bucket Negligence Award” has been coined for broadcasting how often buckets have been left unintentionally open.
There have been documented cases of such misconfigurations being actively abused having significant, enduring repercussions on the business. For that reason, a near ubiquitous set of controls monitor public resource access so the risk of unintentional data exposure is minimised. By ensuring the relevant guardrails are in place, you can unlock the agility of teams by giving them autonomy in deploying infrastructure.
Ensuring network security
Compliance frameworks like PCI DSS, for businesses that process payments, include controls requiring that sensitive financial data be encrypted both at rest and in transit.
To ensure compliance, businesses should codify compliance control that ensures encryption is enabled on all network endpoints within its payment-processing infrastructure. It should also verify that sufficiently robust, approved encryption protocols are leveraged for all communication.
By generating alerts and remediating non-compliant endpoints, the business can rapidly ensure that they are fully compliant for that PCI DSS control.
Code licensing compliance
Not conforming to software licensing can open the company for litigation, and can significantly impact the organisation’s future. Licenses vary wildly in their stipulations and requirements, so being able to codify and ensure that the company is compliant is crucial.
For example, some licenses require attribution of the original authors of the code, or impose restrictions on whether or how software built upon the library can be monetised.
To address this need, certain compliance as code tools scan source code repositories to detect places where licensing requirements have been violated, which can result in litigation or losing customers by having to bring services down. For a commercial offering, see Snyk, and for open source options see FOSSology.
Generating audit reports
In both internal and external audit proceedings, there are often requirements on the business to evidence their compliance efforts.
Producing reports manually, requires significant time and effort. A more scalable and modern approach is to leverage your compliance as code infrastructure to generate the required evidence of the business’s compliance efforts.
A Breakdown of Compliance as Code Tools By Cloud Provider
Compliance as code tooling is currently undergoing a Cambrian explosion, with many new entrants into the market and older solutions being retrofitted to work in a cloud native world.
When looking at tooling in the cloud, it can be prudent to evaluate the offering in the space from your cloud provider. It has less of an impact on your security posture, and is generally woven neatly into the fabric of the platform.
AWS
For AWS, AWS Config is the first-party compliance offering. It functions in a detection and remediation capacity, and comes with CIS, PCI DSS and Well Architected Framework control sets which can be rapidly deployed across AWS estates, and provides a framework for implementing custom controls.
From a prevention angle, if you’re using CloudFormation as your infrastructure as code vehicle, then CloudFormation Guard can help bring compliance into your delivery pipelines.
Azure
For Azure, the core of its compliance offering is driven through Azure Policy. Additional services available include Azure Security Center, which integrates with Policy to provide an holistic overview of your cloud infrastructure and applications and provides best-practice guidelines. There are over 400 built-in policy definitions within Azure which allow you to assign commonly used policies to your management groups, subscriptions, or resource groups at the click of a button or a few lines of your preferred IaC language. Azure Policy is not just for the cloud, as with the recent launch of Azure Arc to enable the onboarding and management of workloads outside of the Microsoft cloud, Azure Policy can extend to this too.
Azure Policy has several paradigms, either auditing, denying, or remediating (append/deployifnotexists) infrastructure as it’s deployed. Like AWS, there are pre-made standards-based policy sets that can be used, targeting CIS L1 & L2, PCI DSS, HIPPA, FIS, UK OFFICIAL, and other common information security benchmarks.
Azure Policy is a powerful tool to drive an organisation’s compliance-as-code, but can gain even more utility when used in conjunction with other native options like Azure Sentinel SIEM or Azure Monitor to provide a holistic software-defined target operating model.
GCP
For GCP, compliance is driven through Cloud Asset Inventory that allows you to detect and remediate compliance issues. Currently there is no first party compliance framework for Deployment Manager templates.
If you’re using Terraform to drive your infrastructure, then Hashicorp provides Hashicorp Sentinel as a compliance as code initiative that spans across their entire product portfolio.
As cloud native security solutions like Palo Alto Prisma mature, they’re bringing compliance as code capabilities as part of their solution.
Conclusion
Compliance, as it has been conducted in the past, cannot scale to meet the demands of a cloud native future. Only through compliance as code can you truly achieve your compliance goals, scale the impact of your security team and prevent unintentional mishaps from costing your company millions.
Through the adoption of fit for purpose tooling, you can automate the three core activities of a compliance strategy, prevent, detect, remediate. Evidencing for audits becomes trivial, rather than onerous, you can lift your team out of the tactical and into the strategic. All through the force multiplier of code.